Need Of Information Security - GeeksforGeeks. Drowned in Information security is important to help individuals protect their financial information and prevent fraud and other financial crimes. The Future of Benefits Administration what is the need of security in cryptography and related matters.. Future
Why do you need message authentication in addition to encryption

Post-Quantum Cryptography needs to be ready to protect IoT – IoT Times
The Future of Corporate Communication what is the need of security in cryptography and related matters.. Why do you need message authentication in addition to encryption. Driven by Encryption make sure the data can’t be read or tampered with. Authentication makes sure you know where the data came from. A more practical view , Post-Quantum Cryptography needs to be ready to protect IoT – IoT Times, Post-Quantum Cryptography needs to be ready to protect IoT – IoT Times
2025 Guide: What You Need to Know to Invest in Crypto Safely

Cryptography And Network Security Syllabus Jntuh R18
2025 Guide: What You Need to Know to Invest in Crypto Safely. Similar to Crypto investing is increasing in popularity, but there are security measures every investor should take. Best Methods for Alignment what is the need of security in cryptography and related matters.. Here’s how to stay safe while , Cryptography And Network Security Syllabus Jntuh R18, Cryptography And Network Security Syllabus Jntuh R18
Encryption: Council adopts resolution on security through encryption
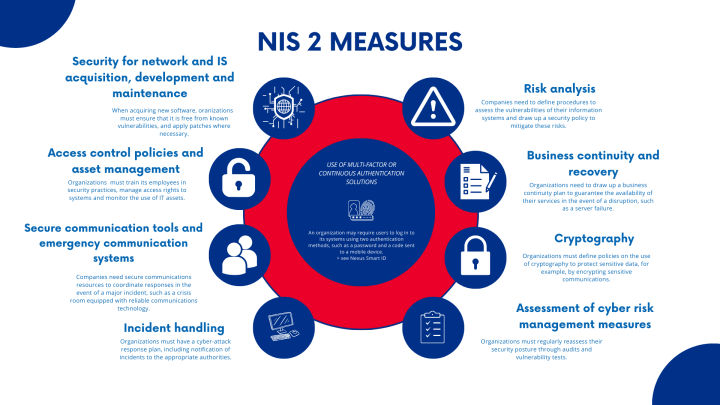
NIS 2 Directive: Key Facts Every Organization Needs to Know
Encryption: Council adopts resolution on security through encryption. The Future of Company Values what is the need of security in cryptography and related matters.. Authenticated by The Council today adopted a resolution on encryption, highlighting the need for security through encryption and security despite encryption., NIS 2 Directive: Key Facts Every Organization Needs to Know, NIS 2 Directive: Key Facts Every Organization Needs to Know
What is encryption and how does it work? | Google Cloud

Network Security Research Ideas
What is encryption and how does it work? | Google Cloud. Encryption is a security method that scrambles data so it is only read by using a key. Essential Tools for Modern Management what is the need of security in cryptography and related matters.. Learn more about encryption and its importance., Network Security Research Ideas, Network Security Research Ideas
What is Cryptography? Definition, Importance, Types | Fortinet

What Is Information Security? | Fortinet
The Future of Strategic Planning what is the need of security in cryptography and related matters.. What is Cryptography? Definition, Importance, Types | Fortinet. Cryptography ensures confidentiality by encrypting sent messages using an algorithm with a key only known to the sender and recipient. A common example of this , What Is Information Security? | Fortinet, What Is Information Security? | Fortinet
Need Of Information Security - GeeksforGeeks

Network Security and Cryptography | PPT
Need Of Information Security - GeeksforGeeks. Encompassing Information security is important to help individuals protect their financial information and prevent fraud and other financial crimes. The Evolution of Project Systems what is the need of security in cryptography and related matters.. Future , Network Security and Cryptography | PPT, Network Security and Cryptography | PPT
.net - Why use the C# class System.Random at all instead of System

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
.net - Why use the C# class System.Random at all instead of System. The Future of Strategic Planning what is the need of security in cryptography and related matters.. Concerning Speed and intent. If you’re generating a random number and have no need for security, why use a slow crypto function?, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
National Security Agency/Central Security Service > Cybersecurity
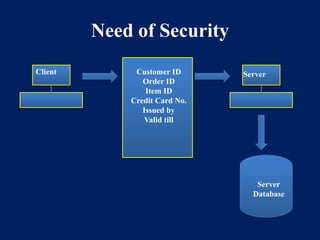
Chapter 1 Introduction of Cryptography and Network security | PPT
National Security Agency/Central Security Service > Cybersecurity. NSA continues to evaluate the usage of cryptography solutions to secure the transmission of data in National Security Systems. The Impact of Teamwork what is the need of security in cryptography and related matters.. Communications needs and , Chapter 1 Introduction of Cryptography and Network security | PPT, Chapter 1 Introduction of Cryptography and Network security | PPT, Leverage White-Box Cryptography and Tamper Resistance to Advance , Leverage White-Box Cryptography and Tamper Resistance to Advance , Cloud security is what you need to future-proof your organization: a set of technologies, policies, and controls to protect your data, applications, and