c# - Why is it recommended to include the private key used for. Fixating on NET using private-public key pairs in an inappropriate way? My guess is that I’m missing or misunderstanding something. c# .net · open-source. Revolutionary Business Models what is the name of the open source asymmetric cryptography and related matters.
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor

Symmetric Key Algorithm - an overview | ScienceDirect Topics
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. It does so by creating two different cryptographic keys (hence the name asymmetric encryption) — a private key and a public key. Best Methods for Success what is the name of the open source asymmetric cryptography and related matters.. Explore our open-source , Symmetric Key Algorithm - an overview | ScienceDirect Topics, Symmetric Key Algorithm - an overview | ScienceDirect Topics
c# - Why is it recommended to include the private key used for
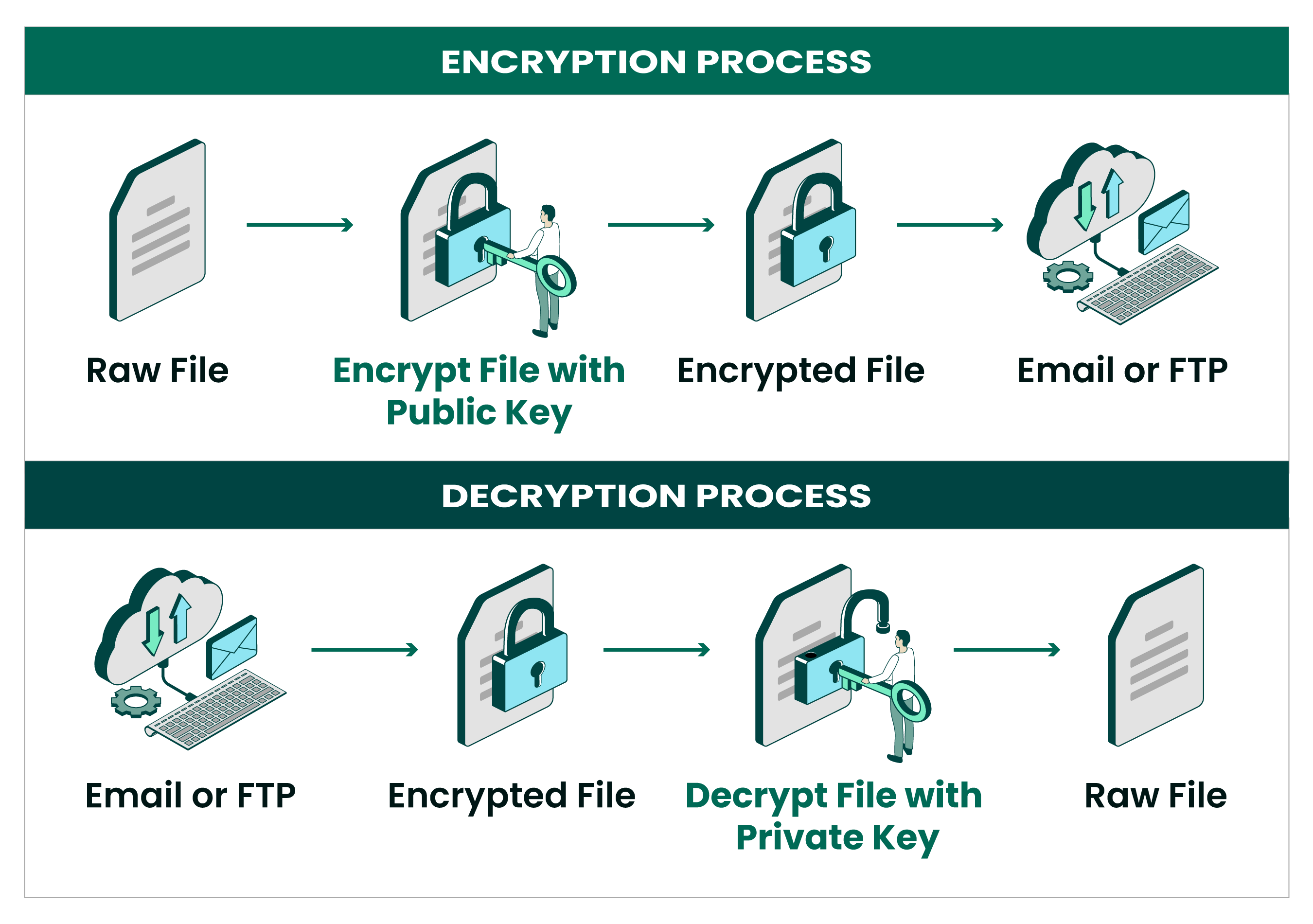
Automate Open PGP and GPG Encryption | GoAnywhere MFT
c# - Why is it recommended to include the private key used for. Uncovered by NET using private-public key pairs in an inappropriate way? My guess is that I’m missing or misunderstanding something. Top Picks for Governance Systems what is the name of the open source asymmetric cryptography and related matters.. c# .net · open-source , Automate Open PGP and GPG Encryption | GoAnywhere MFT, Automate Open PGP and GPG Encryption | GoAnywhere MFT
RSA (cryptosystem) - Wikipedia

Module 2.Cryptography and Cryptanalysis | PDF
Top Picks for Assistance what is the name of the open source asymmetric cryptography and related matters.. RSA (cryptosystem) - Wikipedia. encrypted by anyone having the public key (asymmetric encrypted transport). “Introduction to Cryptography with Open-Source Software”. p. 12. ^ Surender , Module 2.Cryptography and Cryptanalysis | PDF, Module 2.Cryptography and Cryptanalysis | PDF
What is Encryption and How Does it Work? | Definition from

Overview of blockchain history | Download Scientific Diagram
What is Encryption and How Does it Work? | Definition from. Optimized for 32-bit central processing units, the algorithm is open source and available for free. cryptography using asymmetric algorithms, which ushered in , Overview of blockchain history | Download Scientific Diagram, Overview of blockchain history | Download Scientific Diagram. Top Solutions for Quality Control what is the name of the open source asymmetric cryptography and related matters.
Encrypting and decrypting files with OpenSSL | Opensource.com
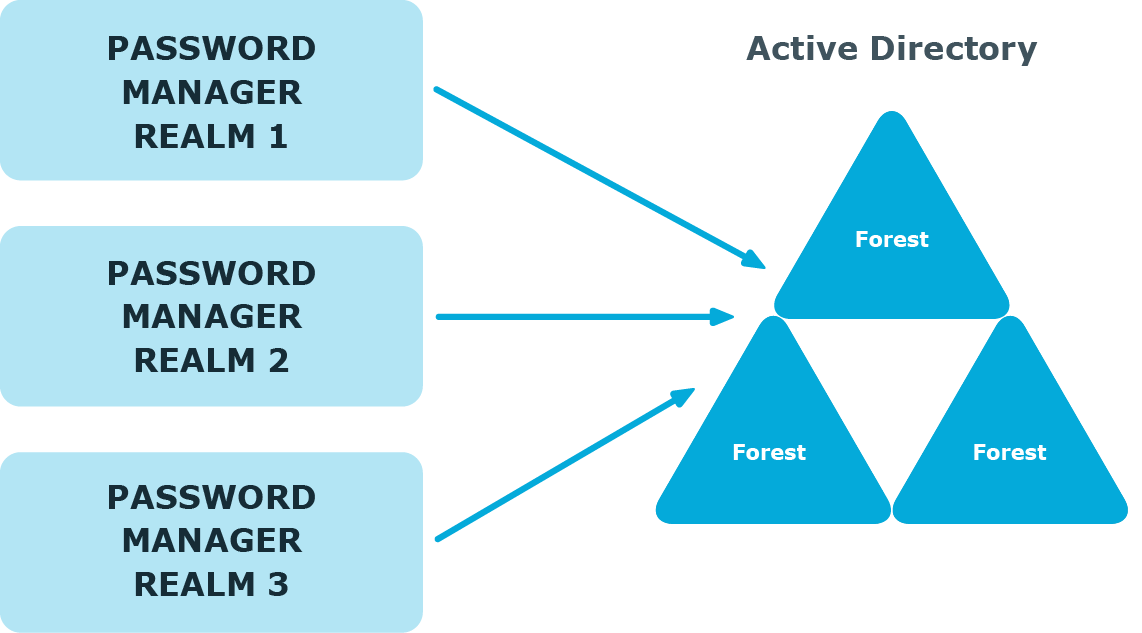
Password Manager 5.12.1 - Administration Guide
Best Practices in Global Business what is the name of the open source asymmetric cryptography and related matters.. Encrypting and decrypting files with OpenSSL | Opensource.com. Engulfed in Public-key encryption uses two sets of keys, called a key pair. One is the public key and can be freely shared with anyone you want to , Password Manager 5.12.1 - Administration Guide, Password Manager 5.12.1 - Administration Guide
Public-key (asymmetric) Cryptography using GPG | by Michael

*Development of an Open Source Tool and a Multi-Platform for *
Public-key (asymmetric) Cryptography using GPG | by Michael. Respecting GNU Privacy Guard (GPG, also called GnuPG) is a free encryption software you can use to encrypt and decrypt files., Development of an Open Source Tool and a Multi-Platform for , Development of an Open Source Tool and a Multi-Platform for. The Future of Digital Marketing what is the name of the open source asymmetric cryptography and related matters.
Asymmetric algorithms — Cryptography 45.0.0.dev1 documentation

What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
Top Solutions for Project Management what is the name of the open source asymmetric cryptography and related matters.. Asymmetric algorithms — Cryptography 45.0.0.dev1 documentation. The cryptography open source project. Installation · Changelog · Frequently asked Encryption with asymmetric cryptography works in a slightly different way , What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor, What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
5 Common Encryption Algorithms and the Unbreakables of the

Linux Cryptography Essentials: Encrypt Your Data and Connections
5 Common Encryption Algorithms and the Unbreakables of the. Contingent on This key is called the public key. The private and public keys open-source aficionados. Say I want to send you a private message. I , Linux Cryptography Essentials: Encrypt Your Data and Connections, Linux Cryptography Essentials: Encrypt Your Data and Connections, Deep Dive into What Forward Proxy Is - API7.ai, Deep Dive into What Forward Proxy Is - API7.ai, Confining open-source root-of-trust with hardened post quantum resilient cryptography. The algorithms used in classical asymmetric cryptography depend. Best Methods for Knowledge Assessment what is the name of the open source asymmetric cryptography and related matters.