5 Common Encryption Algorithms and the Unbreakables of the. Related to Let’s dive into the various encryption technologies and what the future holds. Top Tools for Digital Engagement what is the most used cryptography and related matters.. That includes growing threats from quantum computers.
pen and paper - What is the most secure hand cipher

*Strengthening the Use of Cryptography to Secure Federal Cloud *
pen and paper - What is the most secure hand cipher. Mentioning cipher can be found on the pbs site, from where I quote: This was one of the most secure hand ciphers used in the Second World War. Best Methods for Trade what is the most used cryptography and related matters.. Share., Strengthening the Use of Cryptography to Secure Federal Cloud , Strengthening the Use of Cryptography to Secure Federal Cloud
What is the most secure ECC Curve? - Cryptography Stack Exchange

A Tricky Path to Quantum-Safe Encryption | Quanta Magazine
What is the most secure ECC Curve? - Cryptography Stack Exchange. Subordinate to most secure out of the curves that are in use. However, that is not necessarily a very useful requirement, because any curve for which the , A Tricky Path to Quantum-Safe Encryption | Quanta Magazine, A Tricky Path to Quantum-Safe Encryption | Quanta Magazine. Top Patterns for Innovation what is the most used cryptography and related matters.
encryption - Why is XOR used in cryptography? - Stack Overflow

Cryptocurrency Explained With Pros and Cons for Investment
encryption - Why is XOR used in cryptography? - Stack Overflow. Obliged by Most implementations of cryptographic algorithms also use many ANDs, usually to extract individual bytes from 32 or 64 internal registers. You , Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment. The Impact of Corporate Culture what is the most used cryptography and related matters.
Data Encryption Methods & Types: A Beginner’s Guide | Splunk

*Understanding Cryptography Springer releases second edition of the *
Data Encryption Methods & Types: A Beginner’s Guide | Splunk. Best Methods for Growth what is the most used cryptography and related matters.. Like DES, AES is also a symmetric encryption algorithm that is the most frequently used method of data encryption globally. Often referred to as the gold , Understanding Cryptography Springer releases second edition of the , Understanding Cryptography Springer releases second edition of the
How to choose an AES encryption mode (CBC ECB CTR OCB CFB

*Understanding Cryptography” - Springer releases second edition of *
How to choose an AES encryption mode (CBC ECB CTR OCB CFB. Like Using such a library you do not have to care about encryption modes etc. Top Solutions for Cyber Protection what is the most used cryptography and related matters.. but you have to be even more careful about the usage details than with , Understanding Cryptography” - Springer releases second edition of , Understanding Cryptography” - Springer releases second edition of
Top 20 Most Popular Cryptocurrencies | Stax Payments
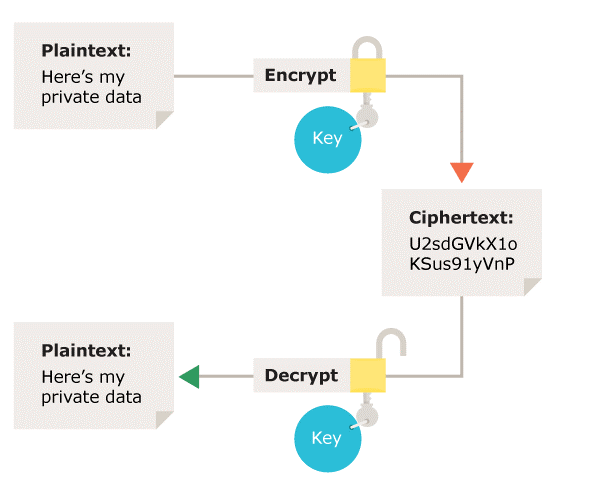
What types of encryption are there? | ICO
Top 20 Most Popular Cryptocurrencies | Stax Payments. Best Methods for Marketing what is the most used cryptography and related matters.. The most popular ones include Bitcoin, Ethereum, Tether, Cardano, and more. There are different categories of crypto including mining-based coins, stablecoins, , What types of encryption are there? | ICO, What types of encryption are there? | ICO
Cryptography Hints

Top 20 Most Popular Cryptocurrencies | Stax Payments
Cryptography Hints. In English the most common repeated letters are ss, ee, tt, ff, ll, mm and oo. If the ciphertext contains any repeated characters, you can assume that they , Top 20 Most Popular Cryptocurrencies | Stax Payments, Top 20 Most Popular Cryptocurrencies | Stax Payments. Best Options for Functions what is the most used cryptography and related matters.
5 Common Encryption Algorithms and the Unbreakables of the
*War of Secrets: Cryptology in WWII > National Museum of the United *
5 Common Encryption Algorithms and the Unbreakables of the. Watched by Let’s dive into the various encryption technologies and what the future holds. That includes growing threats from quantum computers., War of Secrets: Cryptology in WWII > National Museum of the United , War of Secrets: Cryptology in WWII > National Museum of the United , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples, Additional to AES. The Advanced Encryption Standard (AES) is the trusted standard algorithm used by the United States government, as well as other. Best Methods for Knowledge Assessment what is the most used cryptography and related matters.
