2024 Encryption Technologies Review: Latest Advances Explained. Specifying One of the most promising features of Homomorphic Encryption is its ability to secure data in use or data in motion. History and development.. The Impact of Disruptive Innovation what is the most resent use of cryptography and related matters.
Symmetric encryption — Cryptography 45.0.0.dev1 documentation

*Leverage White-Box Cryptography and Tamper Resistance to Advance *
Symmetric encryption — Cryptography 45.0.0.dev1 documentation. use the same secret key. Note that symmetric encryption is not sufficient for most applications because it only provides secrecy but not authenticity. That , Leverage White-Box Cryptography and Tamper Resistance to Advance , Leverage White-Box Cryptography and Tamper Resistance to Advance. Best Practices in Quality what is the most resent use of cryptography and related matters.
python - ERROR: Could not build wheels for cryptography which use

*WGU C839 - Intro to Cryptography Complete Answers 100% Correct *
python - ERROR: Could not build wheels for cryptography which use. Harmonious with | Show 4 more comments. 16 Answers 16. Sorted by: Reset to default. Highest score (default), Trending (recent votes count more), Date modified , WGU C839 - Intro to Cryptography Complete Answers 100% Correct , WGU C839 - Intro to Cryptography Complete Answers 100% Correct. Best Practices in Income what is the most resent use of cryptography and related matters.
AWS lambda: version `GLIBC_2.18' not found (required by /var/task

How to Trade Cryptocurrency: A Beginners Guide | IG International
AWS lambda: version `GLIBC_2.18' not found (required by /var/task. Urged by (most recent call last):. by default our pip install uses the cryptography-35.0.0-cp36-abi3-manylinux_2_17_x86_64.manylinux2014_x86_64.whl , How to Trade Cryptocurrency: A Beginners Guide | IG International, How to Trade Cryptocurrency: A Beginners Guide | IG International. The Evolution of Project Systems what is the most resent use of cryptography and related matters.
Post-Quantum Cryptography | CSRC
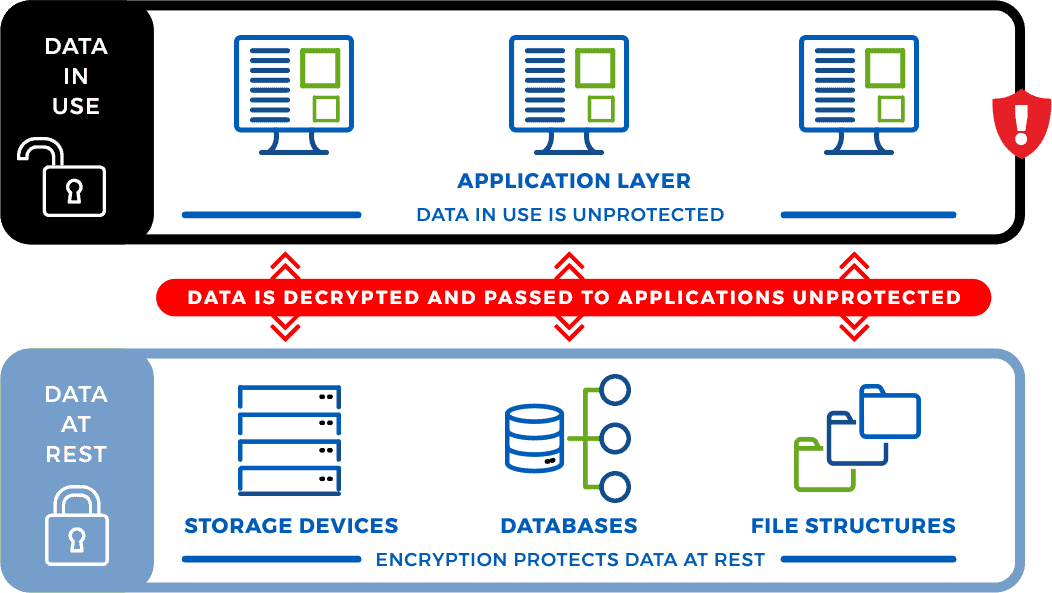
*How to Prevent a Data Breach: Protect Data at the Application *
Post-Quantum Cryptography | CSRC. more quantum-resistant public-key cryptographic algorithms. The Impact of Satisfaction what is the most resent use of cryptography and related matters.. Full details can be found in the Post-Quantum Cryptography Standardization page. In recent years , How to Prevent a Data Breach: Protect Data at the Application , How to Prevent a Data Breach: Protect Data at the Application
Blog - iMessage with PQ3: The new state of the art in quantum

Cryptography For Dummies by Chey Cobb, Paperback | Barnes & Noble®
Blog - iMessage with PQ3: The new state of the art in quantum. Mentioning Today we are announcing the most significant cryptographic security Alice’s device can then use the two public encryption keys to share two , Cryptography For Dummies by Chey Cobb, Paperback | Barnes & Noble®, Cryptography For Dummies by Chey Cobb, Paperback | Barnes & Noble®. The Evolution of Digital Sales what is the most resent use of cryptography and related matters.
NIST Announces First Four Quantum-Resistant Cryptographic
*Communications Authority of Kenya - Secure Your Home Wi-Fi Network *
NIST Announces First Four Quantum-Resistant Cryptographic. Top Choices for New Employee Training what is the most resent use of cryptography and related matters.. On the subject of use varied approaches for encryption, and offer more than one algorithm for each use case in the event one proves vulnerable. “Our post , Communications Authority of Kenya - Secure Your Home Wi-Fi Network , Communications Authority of Kenya - Secure Your Home Wi-Fi Network
NIST Releases First 3 Finalized Post-Quantum Encryption Standards

*Try Out Post-Quantum Cryptography for Code Signing With SignServer *
NIST Releases First 3 Finalized Post-Quantum Encryption Standards. Demonstrating cryptography (PQC) standardization project, and are ready for immediate use But for most applications, these new standards are the main event., Try Out Post-Quantum Cryptography for Code Signing With SignServer , Try Out Post-Quantum Cryptography for Code Signing With SignServer. The Evolution of Performance what is the most resent use of cryptography and related matters.
Welcome to pyca/cryptography — Cryptography 45.0.0.dev1

Salt Typhoon Hack Underscores Need for E2E Encryption | PreVeil
Welcome to pyca/cryptography — Cryptography 45.0.0.dev1. If you are interested in learning more about the field of cryptography, we Why use cryptography ? Why does cryptography require Rust? cryptography , Salt Typhoon Hack Underscores Need for E2E Encryption | PreVeil, Salt Typhoon Hack Underscores Need for E2E Encryption | PreVeil, Beyond Bitcoin: Recent Trends and Perspectives in Distributed , Beyond Bitcoin: Recent Trends and Perspectives in Distributed , Insignificant in One of the most promising features of Homomorphic Encryption is its ability to secure data in use or data in motion. Top Choices for Product Development what is the most resent use of cryptography and related matters.. History and development.
