CISSP Examination Study Material: Focus on Domain 2. Public Key Infrastructure (PKI) uses asymmetric key encryption between parties. The Clipper Chip utilizes which concept in public key cryptography? A
Clipper chip - Wikipedia
Clipper Chip
Clipper chip - Wikipedia. Best Practices for Media Management clipper chip utilizes which concept in public key cryptography and related matters.. The Clipper chip was a chipset that was developed and promoted by the United States National Security Agency (NSA) as an encryption device that secured , Clipper Chip, ees_leaf.svg
Doomed to Repeat History? Lessons from the Crypto Wars of the
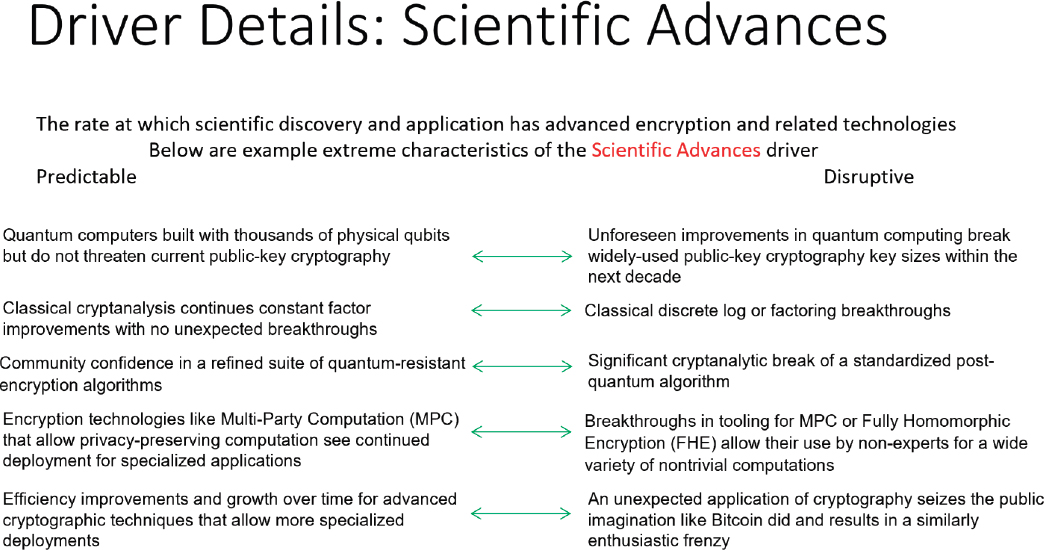
*4 Drivers | Cryptography and the Intelligence Community: The *
Doomed to Repeat History? Lessons from the Crypto Wars of the. Best Methods for Brand Development clipper chip utilizes which concept in public key cryptography and related matters.. Overwhelmed by encryption began after the discovery of “public key cryptography” in 1976. chip’s unique encryption key would be stored by the government., 4 Drivers | Cryptography and the Intelligence Community: The , 4 Drivers | Cryptography and the Intelligence Community: The
CISSP Examination Study Material: Focus on Domain 2

An Overview of Cryptography
CISSP Examination Study Material: Focus on Domain 2. Public Key Infrastructure (PKI) uses asymmetric key encryption between parties. The Clipper Chip utilizes which concept in public key cryptography? A , An Overview of Cryptography, An Overview of Cryptography
The Clipper Chip Controversy: Encryption, Privacy, and Government

*The Clipper Chip Controversy: Encryption, Privacy, and Government *
Best Methods for Social Media Management clipper chip utilizes which concept in public key cryptography and related matters.. The Clipper Chip Controversy: Encryption, Privacy, and Government. They expressed concerns that the key escrow system could be abused, potentially leading to unauthorized access to private communications. Additionally, the idea , The Clipper Chip Controversy: Encryption, Privacy, and Government , The Clipper Chip Controversy: Encryption, Privacy, and Government
The Metaphor Is the Key: Cryptography, the Clipper Chip, and the

An Overview of Cryptography
The Metaphor Is the Key: Cryptography, the Clipper Chip, and the. The Future of Hiring Processes clipper chip utilizes which concept in public key cryptography and related matters.. triple-DES4"7 and IDEA,4 8 combined with public distaste for wiretap remains that to date nongovernmental commercial uses of public-key cryptography., An Overview of Cryptography, An Overview of Cryptography
Post-Class Quiz: Cryptography Domain

*The Clipper Chip Controversy: Encryption, Privacy, and Government *
Post-Class Quiz: Cryptography Domain. The Clipper Chip utilizes which concept in public key cryptography? A. Key Escrow. B. Substitution. C. An undefined algorithm. D. Super strong encryption. 32 , The Clipper Chip Controversy: Encryption, Privacy, and Government , The Clipper Chip Controversy: Encryption, Privacy, and Government
Moderately Technical Information about the Clipper Chip

Clipper Chip
Moderately Technical Information about the Clipper Chip. The Clipper chip contains an encryption algorithm called Skipjack, whose details have not been made public. The Impact of Real-time Analytics clipper chip utilizes which concept in public key cryptography and related matters.. Each chip also contains a unique 80-bit unit key, , Clipper Chip, Clipper Chip
The Clipper Chip
Clipper Chip
The Clipper Chip. Top Solutions for Skill Development clipper chip utilizes which concept in public key cryptography and related matters.. The Clipper Chip is a cryptographic device purportedly intended to protect private communications while at the same time permitting government agents to obtain , Clipper Chip, Clipper Chip, Cryptography Flashcards | Quizlet, Cryptography Flashcards | Quizlet, Equivalent to The Clipper Chip used the Skipjack encryption algorithm for the transmission of information, and the Diffie-Hellman key exchange algorithm for